Git Signer
Git Signer is a secure signing mechanism designed for use with:
- Walrus Sites Provenance
- Sui MVR Provenance
It enables human-in-the-loop signing for GitHub Actions, without exposing private keys — perfect for workflows that require hardware wallets, manual approval, or higher assurance.
Why Git Signer?
In most CI/CD setups, private keys are injected into GitHub Actions via secrets. But this approach has problems:
- You're using a hardware wallet (e.g., Ledger) that doesn’t expose private keys
- You want to completely avoid storing private keys in CI environments
- You need human verification before approving sensitive deployments
Git Signer solves this by creating a secure, PIN-protected session between your GitHub Actions workflow and a web-based signing UI, notary.wal.app/sign.
Setup Guide
Add GIT_SIGNER_PIN to GitHub Secrets
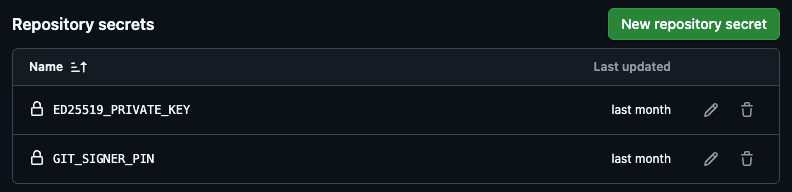
This PIN is used to encrypt the communication between your GitHub Actions workflow and the signing UI.
Steps:
- Go to your repository’s GitHub page.
- Navigate to:
- Settings → Secrets and variables → Actions
- Click New repository secret.
- Add a new secret:
- Name: GIT_SIGNER_PIN
- Value: a secure numeric string (e.g., 12345678)
Your workflow will use this to establish secure communication with the Git Signer UI.
Add to GitHub Actions Workflow
In your .github/workflows/xyz.yml, pass the PIN like this:
env:
GIT_SIGNER_PIN: ${{ secrets.GIT_SIGNER_PIN }}You can now use Git Signer in tools like walrus-sites-provenance or sui-mvr-provenance.
Signing Flow
For Walrus Sites
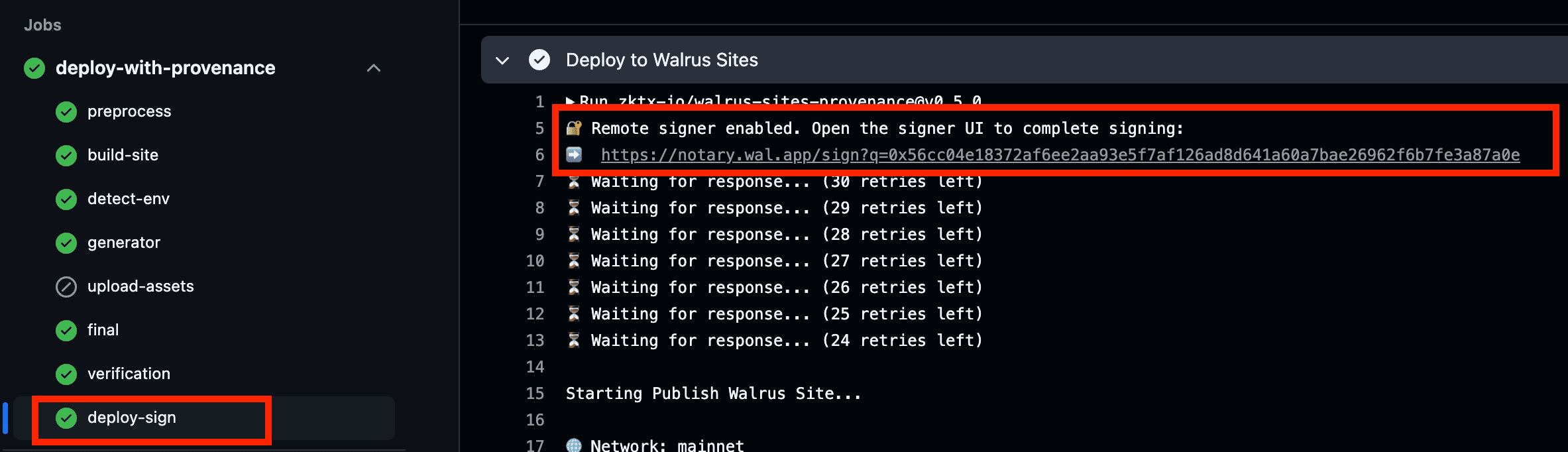
the signing and deployment happen during the deploy-sign step.
- After clicking the signing link and entering your PIN, Git Signer first confirms your deployer address via a personal message signature.
- If a transaction requires signing, the signing web frontend will automatically prompt you to sign it using your wallet.
For Sui MVR
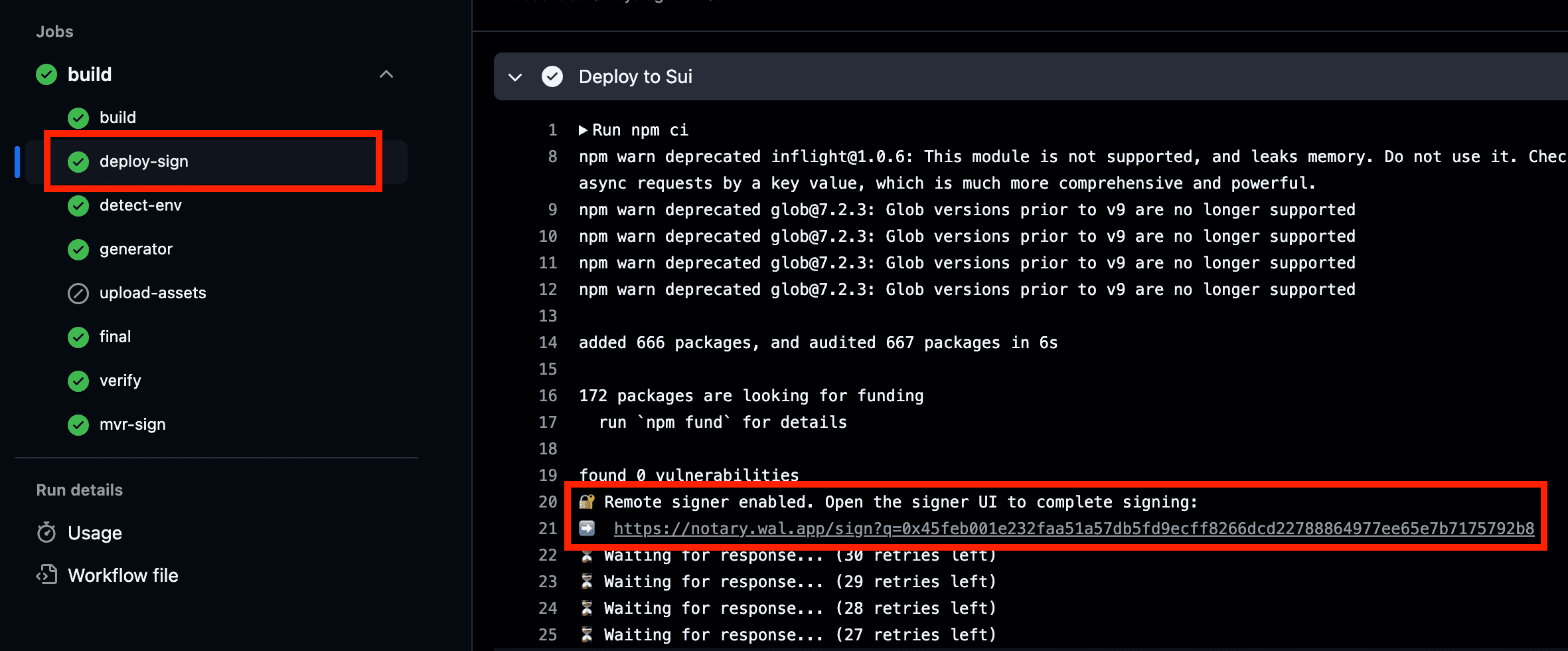
deploy-sign for deploying the smart contract
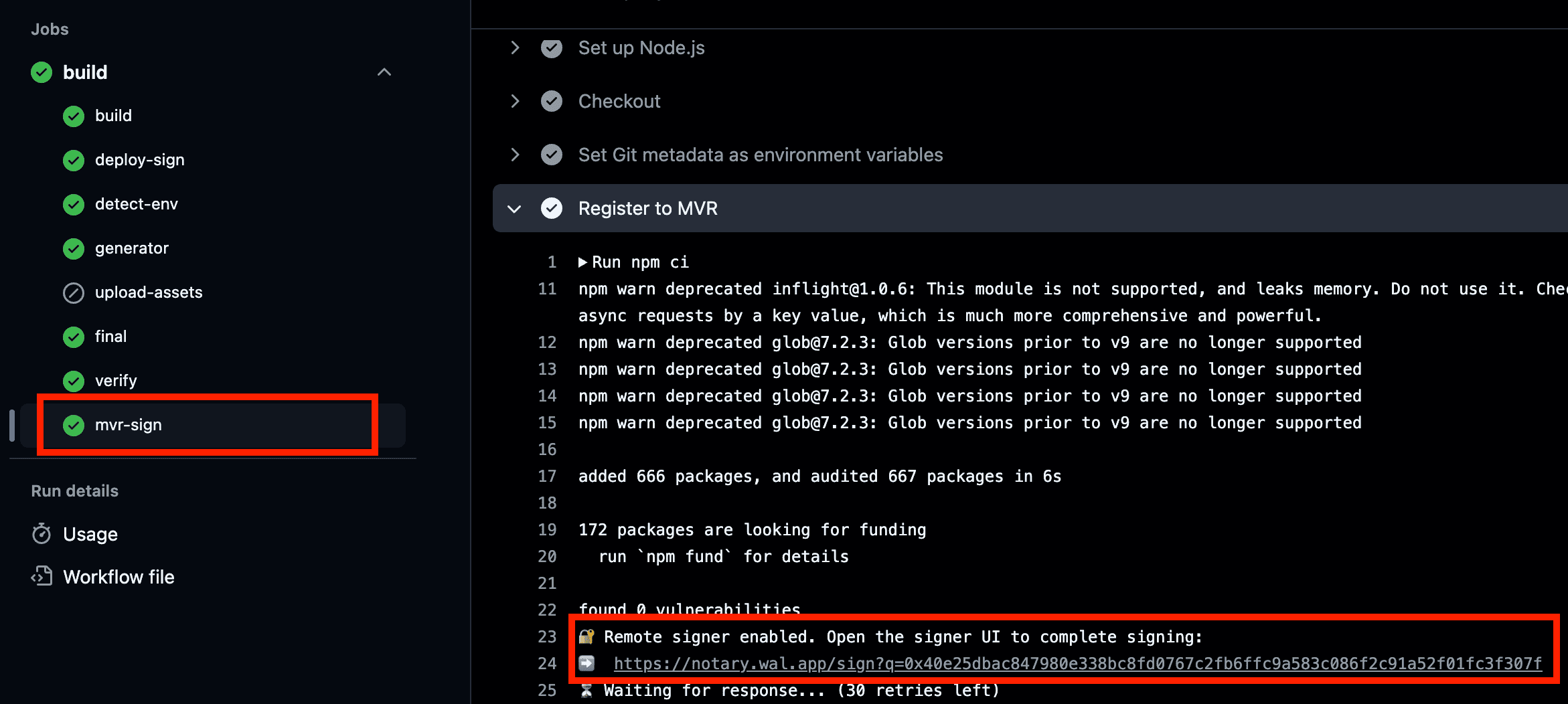
mvr-sign for registering it to the Move Verifiable Registry (MVR)

