SLSA on Blockchain
Introduction
The integrity of the software supply chain has become critical across open-source and Web3 ecosystems.
In the context of blockchain, users and auditors need guarantees that what was built and what was deployed are identical and untampered.
This section introduces how SLSA can be applied to blockchain development, particularly for verifiable deployments of smart contracts and static sites using Walrus.
What is SLSA?
SLSA (Supply-chain Levels for Software Artifacts) is a security framework developed by Google, OpenSSF, and other foundations.
It defines progressive levels of supply chain integrity, helping developers build and distribute software in a verifiable, tamper-resistant way.
SLSA Security Levels
- Build L0 – Basic version control
- Build L1 – Build script consistency and traceability
- Build L2 – Build provenance and signed attestations
- Build L3 – Hardened, isolated, and auditable build environment
GitHub Actions and Google Cloud Build are certified for SLSA Level 3.
Real-World Example: npm Package Provenance
One real-world application of SLSA is npm package provenance, supported by GitHub.
This mechanism allows users to:
- Verify that a published npm package was built from a specific GitHub workflow
- See the exact commit and repository it came from
- Confirm that the package hasn’t been modified after build
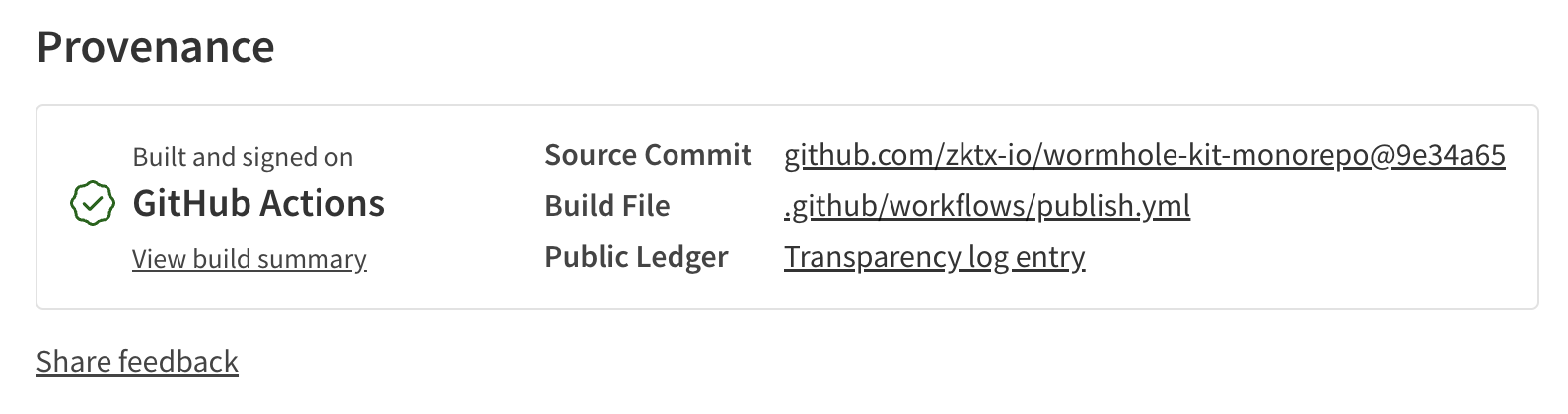
This level of transparency and trust — originally introduced for Web2 — is now extended to Web3 deployments through our integration of SLSA with smart contract and frontend deployments.
Bringing SLSA to Blockchain
By integrating SLSA into the build and deployment workflow for blockchain applications, we enable:
- Reproducible builds
- Verifiable build environments
- Auditable deployment provenance
- Tamper detection for on-chain resources
The rest of this section will explore how Walrus, Sigstore, and GitHub Actions work together to bring this to life.

