Introduction & SLSA Overview
Verifiable Blockchain Deployments with SLSA
Secure your smart contracts and frontend deployments with verifiable provenance and GitHub-based signing. This documentation explains how the SLSA framework can be applied to blockchain development using GitHub Actions, Sigstore, and on-chain verification tools.
Why It Matters
In Web3, it's critical to prove that the code you deployed is exactly what you built. Without verification, users and auditors must rely on trust — something the blockchain was meant to eliminate.
By combining:
- ✅ SLSA (Supply-chain Levels for Software Artifacts)
- ✅ GitHub provenance using Sigstore
- ✅ Walrus for decentralized site hosting
- ✅ GitSigner + Notary for external signing and verification
...you can now deliver tamper-proof, auditable, and cryptographically verifiable deployments for both frontend and smart contract projects.
What is SLSA?
SLSA (Supply-chain Levels for Software Artifacts) is a framework developed by Google, OpenSSF, and the broader OSS community. It defines a progressive model for software supply chain integrity, from basic version control to hardened, auditable build pipelines.
SLSA Security Levels
| Level | Description |
|---|---|
| L0 | No guarantees — just version control |
| L1 | Build scripts are consistent and recorded |
| L2 | Build provenance is captured and signed |
| L3 | Build is run in a hardened, tamper-resistant environment |
GitHub Actions and Google Cloud Build are certified to reach SLSA Level 3.
From Web2 to Web3: Why Blockchain Needs SLSA
SLSA was first applied to ecosystems like npm, where users could verify:
- The exact GitHub workflow and commit a package came from
- That the package hasn't been modified post-build
We're now extending that same level of verifiability to:
- 🔐 Smart contract deployments (via Move + MVR)
- 🌐 Static frontend deployments (via Walrus Sites)
In both cases, build provenance is captured, signed, and stored — allowing anyone to verify what was built, who signed it, and whether it matches what's on-chain.
Real-World Example: npm Provenance
One real-world application of SLSA is npm package provenance, supported by GitHub.
This mechanism allows users to:
- ✅ Verify that an npm package was built from a specific GitHub workflow
- ✅ See the exact commit and repository it came from
- ✅ Confirm that the package hasn’t been tampered with after build
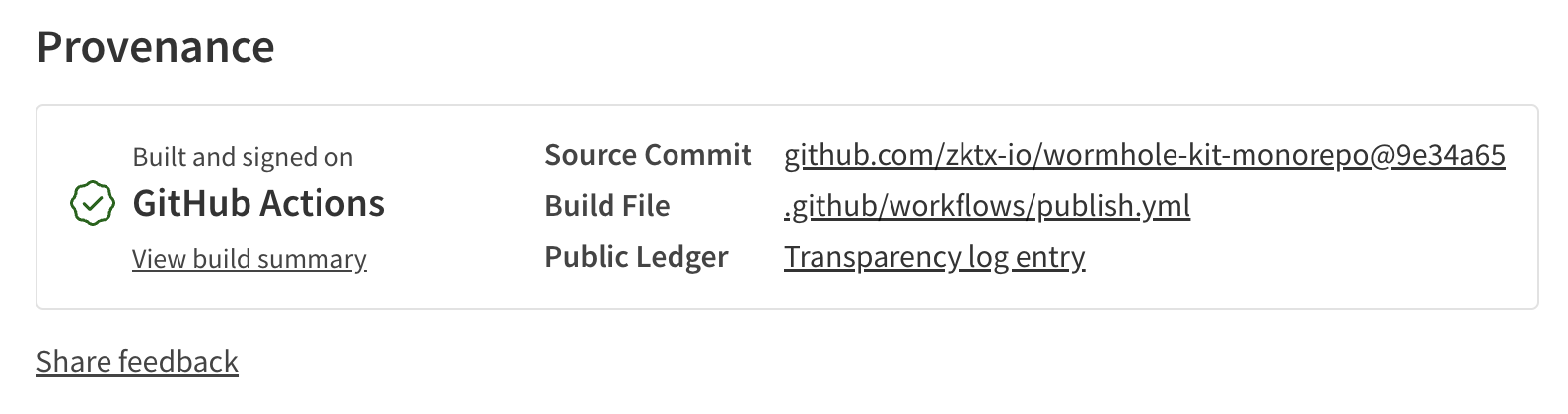
This level of transparency — once exclusive to Web2 ecosystems — is now extended to on-chain deployments through Walrus and MVR.
What You'll Find in This Documentation
This guide includes:
Walrus Sites Provenance How to deploy verifiable static sites to the Sui blockchain.
Sui MVR Provenance How to publish smart contracts with signed provenance metadata.
Verification with Notary A browser-based UI to validate deployments and signatures.
GitSigner A secure PIN-based signing interface to keep private keys out of CI environments.
All tools are modular and interoperable — deploy with one, verify with another.

